Author: SocialXYZ
Where is the Whitespace?
In 2008, the 700MHz spectrum was reallocated to free up transmission bandwidth. There was an initial auction for control of specific blocks of bandwidth and even Google joined the bid.
Google’s intention was never to take control of the airwaves, but to bid the price high enough to mandate open access across the spectrum. This would allow any internet service providers to acquire wireless services on a wholesale basis from block owners and then resell them to customers. While this is certainly better than complete control by those major telecom giants (AT&T and Verizon), I am still waiting to see benefits for end-users…
Phony
Well, I held out as long as I could, but after a fall from my bedside, I was in desperate need of a new phone. My initial goal (going on six months) was to hold out for the Moto X phone, but, unfortunately, it was not to be. Instead, I picked up the pricey Samsung Galaxy S4 and made the switch to Verizon.
My biggest disappointment so far has been the overwhelming amount of bloatware that both Verizon and Samsung install on these devices before shipping. Having had the last Samsung Nexus, the transition is quite obvious. It is unfortunate that a user can only disable most of the bloatware and not uninstall it. And while I am still futzing around with Samsung Gestures, I am largely debating rooting the device to get the raw Android experience. Time will tell.
Some may ask what’s the point in getting a Samsung if you are going to wipe it with stock Android. But it’s a simple answer, it’s for the hardware. Samsung has done their part on providing customers with the best hardware available. But I believe it should be up to the customer to decide what software experience they desire. This was my initial quaff with Apple, who controlled the entire user experience, for good and for bad. The nice thing about Android devices is that the savvy user can decide for themselves which experience they prefer…
In the meantime, I’ll keep fooling around with the Samsung experience and see how it takes…

Fingers Crossed for HICSS-47
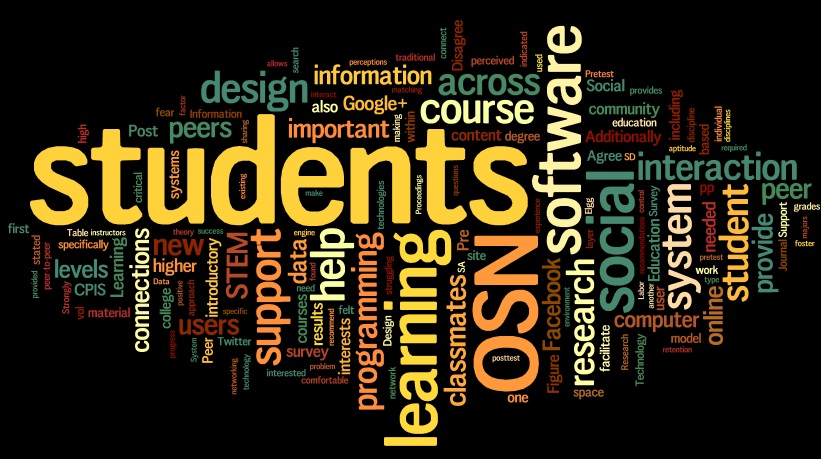
Well, it’s that time of year again for another HICSS submission. I ran into some financial difficulty last year that prevented me from attending HICSS-46, but I am re-determined to make it back in 2014, should they have me. Below is the tag cloud generated using Wordle, which I think is such a fun feature. In fact, I require my students to submit a tag cloud of their final papers to the discussion board for the class to view. I was a bit surprised by the output of this cloud since I was excepting to see ‘peer’ and ‘support’ to be a much larger font. In any case, I have also attached the abstract below.
Abstract
In this paper we explore the design and preliminary evaluation of an online peer-to-peer support system for higher education. Our software utilizes existing online social networking (OSN) software to provide students with a multi-dimensional peer-to-peer support structure. More specifically, this research introduces an innovative expansion to online course learning software that enhances communication based on a student’s course activity including course grades and level of technical skill. We measure the impact of our system across introductory college computer programming courses, taken by traditional college students. Initial survey data was positive and while overall levels of agreement fell between pretest and posttest surveys, the majority of students responded favorably to the new system.
Frenemy at the Gate
 Last week the Guardian made claims that it received classified documents from a whistleblower stating the National Security Agency construction of a massive surveillance machine that has direct access to digital data from sites such as Facebook, Google, Apple and Yahoo.
Last week the Guardian made claims that it received classified documents from a whistleblower stating the National Security Agency construction of a massive surveillance machine that has direct access to digital data from sites such as Facebook, Google, Apple and Yahoo.
What I find interesting is that we all seem to be surprised. The NSA has been collecting data since it was founded in the 1950s. And thanks to legislation that passed under the Bush administration, and renewed under the current administration, it is perfectly legal for government agencies to monitor all data channels.
Now, while I think we should investigate the extent to which the government has direct access to information, what amuses me is the general insecurity of our security agencies. While leaking classified documents is certainly a no-no in their eyes, why are they so afraid that we know this. The lack of transparency only fuels the conspiracy theories. But with a budget of well over $10 billion, I’m sure they won’t be losing too much sleep over it. And if they are, all they really need to do is tap into any phone call I have with my mom… That will put them right to bed.
Then again… There was an interesting article written a few months back discussing the challenges the Drug Enforcement Agency was having to decrypt Apple’s iMessage transmissions due to its encryption scheme. Hmmm….
Maybe I will get that new iPhone after all.